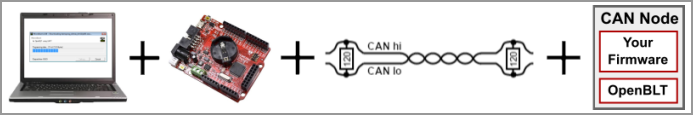
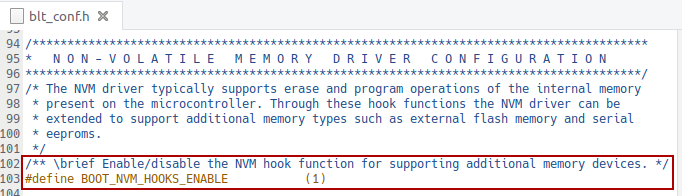
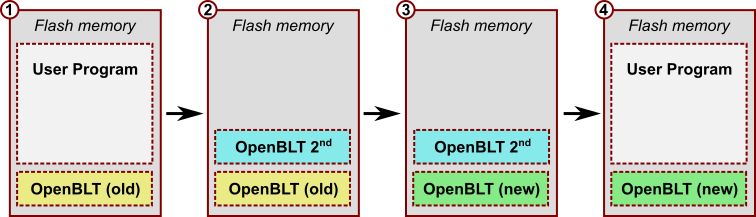
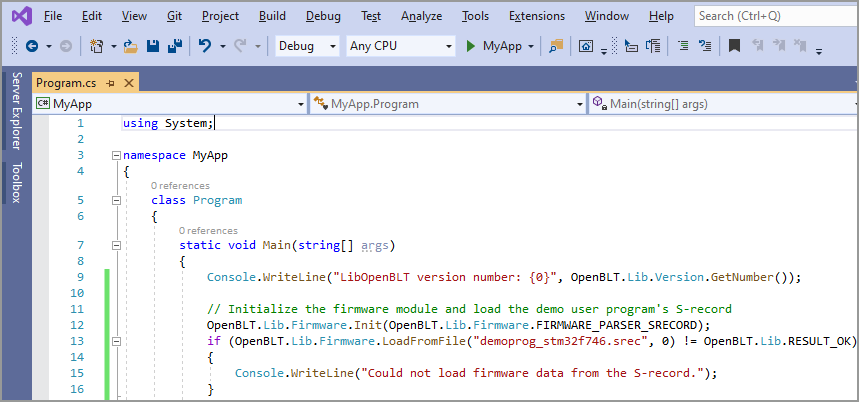
The OpenBLT 1.18.0 release was made today, after another half year of development work. 17 tickets were processed, which resulted in 32 commits. Feel free to download the new version of the OpenBLT bootloader and give it a try. This release is on track with the standard release cycle.

“Mostly maintenance and a few new features” best summarizes the new OpenBLT release. This article provides detailed information of what you can expect from the newly released OpenBLT version 1.18.0.
Continue reading